API Security Best Practices for Developers: Easy Guide to Safe Code
APIs help apps talk and share data. But bad guys try to break them. API Security Best Practices for Developers keep your work safe. You must think about security from the start. In 2025, more attacks hit APIs. Stats show 42% of firms find hidden APIs after hacks. This guide shows easy ways to stop threats. You will learn auth, limits, checks, and watch. These fit REST and other APIs. New coders can use them. Pros can check their ways. Good security stops leaks and down time. Start now for strong apps1.
Why Follow API Security Best Practices for Developers
API Security Best Practices for Developers matter because APIs hold key data. One weak spot lets in bad access. In 2025, bot hits on APIs jumped 372%. You build safety from day one. This cuts fixed time later. Good ways like least give stop big harm. Encrypt hides info from spies. Watch logs catch odd acts fast. Teams with these have less breaks. For example, use a gateway to block bad calls. This keeps your app up. New devs learn quickly with lists. Pros are used to teach teams. Security now part of code not added on. It helps meet rules like GDPR. Safe APIs make users trust you more. Start small and add one way at a time.Many missed basics lead to leaks. Like no check input cause injection. Or weak keys easily crack. API Security Best Practices for Developers fix this. Use strong tools and checks. In DevOps, auto test security. This finds holes early. Good habits save money. One breach cost lots. Think zero trust no one safe. Check all calls. This stops inside bad too. For micro apps, secure talk key. Use tokens right. Learning these will make you a better coder.
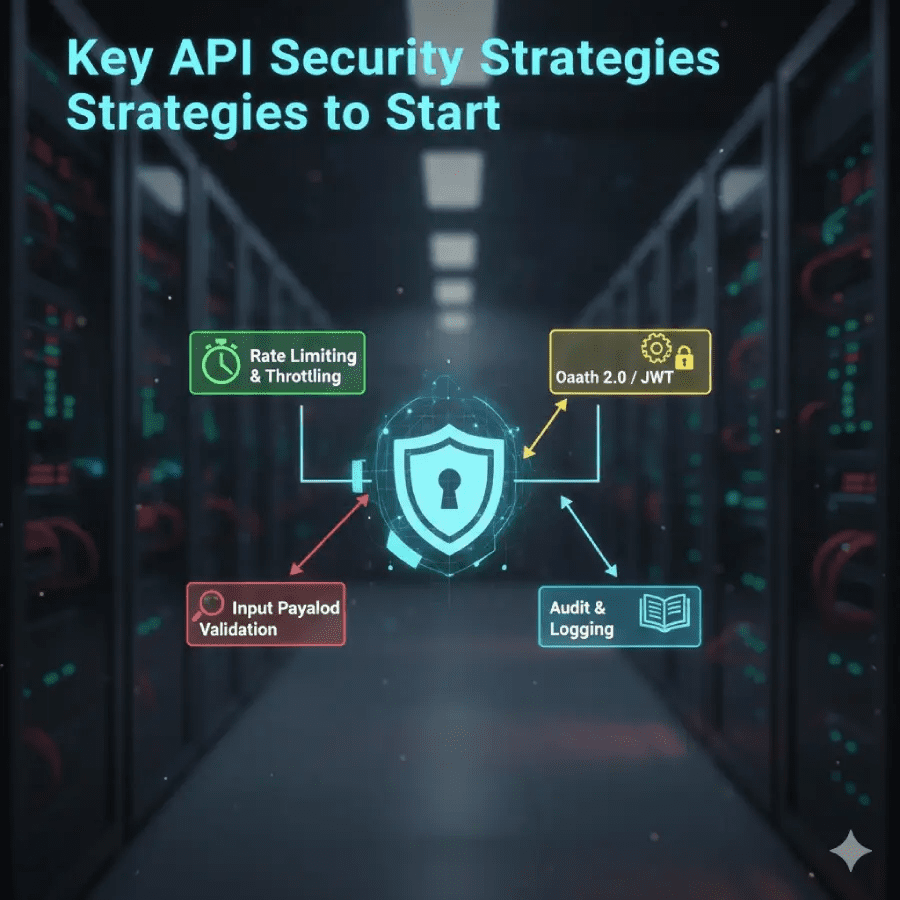
Key API Security Strategies to Start
API security strategies build strong walls. First, know threats like take over or flood. Plan to stop them. Use HTTPS always for safe send. Add certs for trust. For auth, pick OAuth or API keys. OAuth is good for users. Keys for machines. Set a short life for tokens. This cuts risk if stolen. Add rate limits to stop too many calls. Like 100 per min. Block bad IPs. Validate all input. No trust in user data. Clean it to stop the injection. Log all acts but no secret info. Watch logs for odd. Use tools like WAF to block attacks. These API security strategies work for small or big apps.2025, AI helps spot bad. But you set rules. For REST, check verbs like GET no change. POST needs auth. GraphQL hard, limit deep. API security strategies include tests often. Use scans like ZAP. Fix fast. Train team on new threats. Share stories of breaks. This keeps all sharp.
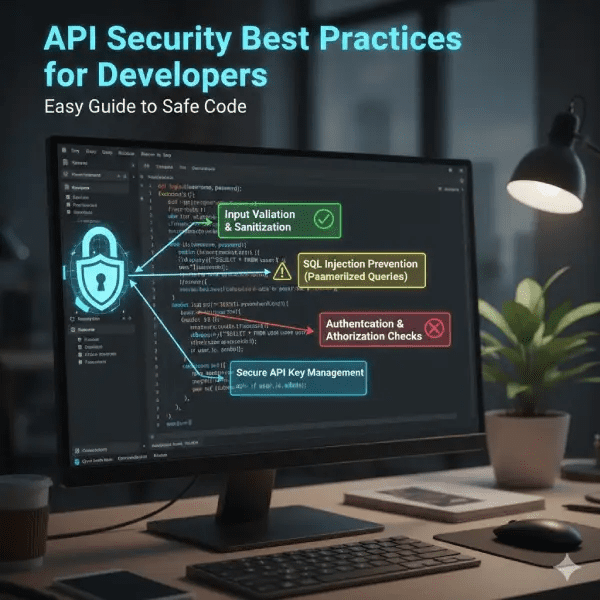
Secure API Development from the Start
Secure API development means safety in design. Draw threats first. See where bad can hit. Use the least give always. Give just need right. For example, read only and not write. Pick safe libs, no old bugs. Code clean no hard keys. Use env vars. Add headers like CSP, no bad script. For files, check type and size. No run bad. In code, hash passes no plain. Salt them too. Secure API development stops many holes. Test as you build. Not waiting for the end.For teams, review code together. Catch bad early. Use auto tools in the pipe. Like scan on push. This makes a secure API development habit. In 2025, shift left means security early. Please do not add later. Good for speed.
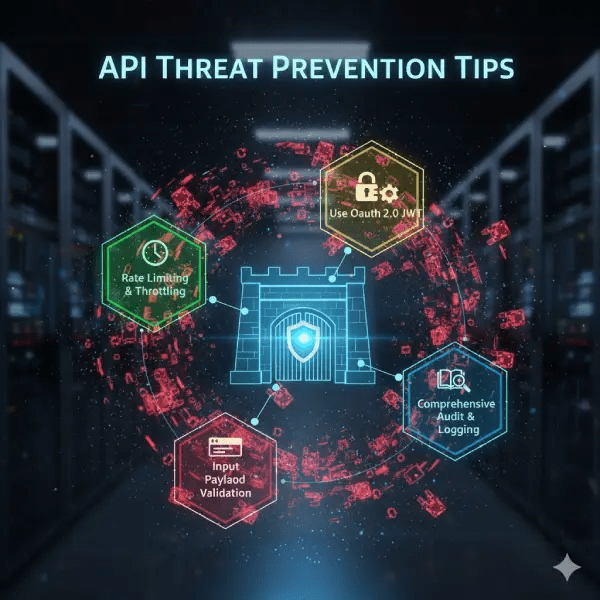
API Threat Prevention Tips
API threat prevention stops bad before it hits. Know OWASP top 10 for APIs. Like broken auth or too much data. Fix with checks. Use gateway for all calls. It adds auth and limits. Block odd patterns. For DDoS, use cloud shields. They take hits. Shadow APIs hide risks. Find all with scans. Zombie old ones close. API threat prevention needs watch 24/7. Set alerts for spikes. Check logs daily.AI bots are smart now. Use CAPTCHA or behavior check. For the supply chain, check libs often. Use tools like Snyk. API threat prevention keeps apps safe for a long time.
REST API Security Practices Made Easy
REST API security practices fit common apps. Use verbs right. GET safe no change. POST check auth. Add CORS headers limit sites. No all stars. For params, validate type and size. No SQL in. Use prepare state. Return the right codes. 401 no auth. 403 no right. Log fails. REST API security practices include version paths. Like v1/users. Change safely. Use HTTPS no HTTP.For data, mask secrets. Like hide cards but last 4. REST API security practices help mobile and web.
OAuth and JWT Best Practices for Tokens
OAuth and JWT best practices keep access safe. OAuth for user flow. JWT for state less. Use OAuth server central. No make own. For JWT, a strong secret. Short time to live. No algo from head. Set back end. No sensitivity in payload. Small size. For OAuth, check the redirect safe. Use state no CSRF. Default scope small. OAuth and JWT best practices stop taking over.Rotate keys often. Use JWKS share. OAuth and JWT best practices are good for scale.
Authentication and Authorization in APIs
Authentication and authorization in APIs split who and what. Auth check who. Like login. Author check can do. Like RBAC roles. Auth first. Use multi factor for strength. No basic auth plain. Authentication and authorization in APIs use claims in tokens. Like user roles. Fine grain with ABAC attrs.Check at gate and API. Double safe. Authentication and authorization in APIs stop wrong access.
Secure Microservices Communication
Secure microservices communication needs trust. Use mTLS certs both ways. Not just HTTPS. Service mesh like Istio adds auto. Encrypt inside too. No trust net. For calls, use tokens scope small. No forward all. Exchange for new. Secure microservices communication stops side move if one breaks.Log calls between. Watch slow or fail. Secure microservices communication key for cloud.
API Access Control Methods
API access control methods limit who in. RBAC roles are easy. ABAC rules on attrs. Like time or IP. Use scopes coarse. Claims fine. Deny default. Allow only matches. API access control methods include auditing who did what.For third parties, register clients. Check them. API access control methods make safe sharing.
API Vulnerability Mitigation Ways
API vulnerability mitigation fixes holes. For inject, validate all. Clean input. For broken auth, strong check. No weak pass. For too expose, return need only. Mask rest. Regular scans. Patch fast. API vulnerability mitigation uses OWASP guide.Test pen often. Fix quick. API vulnerability mitigation keeps up to date.
API Security Guidelines for All
API security guidelines say use zero trust. Check it all. Encrypt every. Log but safe. Monitor odd. Update always. Train team. Follow standards like OAuth. API security guidelines include checklist start.Review often. API security guidelines help no miss.
Rate Limiting and Throttling
Rate limiting and throttling stop flood. Set calls per time. Like 100 hours. Block over. Use a token bucket. For users, diff limits. Free less, pay more. Rate limiting and throttling in the gate are easy.Watch patterns. Block bad. Rate limiting and throttling save server.
Input Validation and Sanitization
Input validation and sanitization clean data. Check type, size, format. No script. Use libs safe. For JSON, parse strict. No extra. Input validation and sanitization stop inject SQL or XSS.Do all ends. Input validation and sanitization base safe.
HTTPS and SSL/TLS for APIs
HTTPS and SSL/TLS for APIs hide data. Use TLS 1.3. Not old. HSTS force HTTPS. Certs from trust CA. Renew time. HTTPS and SSL/TLS for APIs stop in the middle.Pin certs if needed. HTTPS and SSL/TLS for APIs must all.
API Logging and Monitoring
API logging and monitoring see what happens. Log calls, errors, no secrets. Use ELK stack. Set alerts spike or fail. API logging and monitoring catch bad early.AI helps find odd. API logging and monitoring for audit too.
Token-Based Authentication
Token-based authentication no session. Use JWT or opaque. Short life. Secure store. No browser if you can. Token-based authentication scales well.Validate always. Token-based authentication flex.
Role-Based Access Control (RBAC)
Role-based access control (RBAC) gives rights by role. Like admin all, user some. Easy to manage. Check in code. Role-based access control (RBAC) scale groups.Update roles time. Role-based access control (RBAC) base auth.API Gateway SecurityAPI gateway security front door. Add auth, limit, log. Use Kong or AWS. Policy central. API gateway security block bad before API.Update rules. API gateway security must be big apps.Secure Data TransmissionSecure data transmission encrypt all. Use HTTPS. For files, chunk safe. No plain. Secure data transmission stop leak.Compress if needed. Secure data transmission fast and safe.
Identity and Access Management (IAM)
Identity and access management (IAM) handles who in. Use Okta. MFA add. Identity and access management (IAM) central control.Audit access. Identity and access management (IAM) for cloud good.Preventing API Injection AttacksPreventing API injection attacks validate strictly valid. Use params bind. No concat string. Preventing API injection attacks test fuzz.Libs help. Preventing API injection attacks is a common fix.
How to Secure APIs Using Best Practices for Developers
How to secure APIs using best practices for developers’ start plan2. Think of threats. Use strong auth. Validate all. Limit calls. Encrypt. Watch. Test. How to secure APIs using best practices for developers checklist help.Update code. How to secure APIs using best practices for developers ongoing.
API Security Guidelines for REST and GraphQL
API security guidelines for REST and GraphQL same base. REST verbs check. GraphQL limits deep. Both auth tokens. API security guidelines for REST and GraphQL validate query.Tools differ a bit. API security guidelines for REST and GraphQL cover both.Best Authentication Methods for API SecurityBest authentication methods for API security OAuth JWT. API keys are simple. MFA is strong. Best authentication methods for API security pick fit.No basic. Best authentication methods for API security secure.
Preventing Common API Vulnerabilities Like Injection and Broken Auth
Preventing common API vulnerabilities like injection and broken auth validate bind. Strong check. Preventing common API vulnerabilities like injection and broken auth test often.Follow OWASP. Preventing common API vulnerabilities like injection and broken auth key.
Step-by-Step API Security Best Practices for Developers
Step-by-step API security best practices for developers 1 auth. 2 validate. 3 limit. 4 encrypt. 5 log. 6 tests. 7 update. Step-by-step API security best practices for developers easily follow.Do all. Step-by-step API security best practices for developers to build habits.
Tools and Techniques to Monitor API Security Threats
Tools and techniques to monitor API security threats use Splunk ELK. AI anomaly. Tools and techniques to monitor API security threats alert fast.Scan regularly. Tools and techniques to monitor API security threats watch.Implementing Rate Limiting and Input Validation in APIsImplementing rate limiting and input validation in APIs use middleware. Libs help. Implementing rate limiting and input validation in APIs code easy.Test work. Implementing rate limiting and input validation in APIs must.
Secure API Design Principles for Microservices
Secure API design principles for microservices zero trust. mTLS. Scope small. Secure API design principles for microservices gate use.Monitor between. Secure API design principles for microservices scale safe.How Developers Can Protect APIs from Unauthorized AccessHow developers can protect APIs from unauthorized access auth strongly. Check it all. How developers can protect APIs from unauthorized access log fails.Block bad. How developers can protect APIs from unauthorized access easily.
API Security Checklist for Professional Developers
API security checklist for professional developers auth yes. Encrypt yes. Validate yes. Limit yes. Log yes. Test yes. Update yes. API security checklist for professional developers print use.Check often. API security checklist for professional developers guide.
FAQs About API Security Best Practices for Developers
What are top API Security Best Practices for Developers?
Top API Security Best Practices for Developers start with strong auth like OAuth. Add rate limits to stop floods. Validate all input no injections. Encrypt data with HTTPS. Log and watch for odd. Use a gateway for an extra wall. Test regular find holes. These keep APIs safe from common bad. In 2025, add AI watches. For new devs, learn one time. Pros use all.
How do OAuth and JWT best practices help?
OAuth and JWT best practices help safe access. OAuth for user flow no make own. JWT for tokens small and not sensitive. Short live rotate keys. No algo from head. These stops take over. Use JWKS share keys. Central server issue. OAuth and JWT best practices scale well no session.
What REST API security practices to use?
REST API security practices always include HTTPS. Auth for POST PUT. Validate params. Limit calls. Headers are secure like CSP. Return codes right. Log acts. These stop bad verbs. For REST, check content type. REST API security practices easily add middleware.
How does preventing API injection attacks work?
Preventing API injection attacks work with validate clean input. Use bind params no string join. Libs help. Test fuzz find. No trust data. For SQL noSQL same. Preventing API injection attacks base for safety.
What tools and techniques to monitor API security threats?
Tools in tools and techniques to monitor API security threats like ELK log. WAF block. ZAP scan. AI anomaly. Alert Slack. Scan libs. Tools and techniques to monitor API security threats watch 24/7.
Conclusion: Use API Security Best Practices for Developers Now
In sum, API Security Best Practices for Developers keep your work safe and strong. From auth to watch, these ways stop bad acts. In 2025, threats grow but tools help. Start small add more. Safe APIs win trust. Teams better with them. What one practice you add today?
References
- Curity API Security Best Practices – 16 practices like gateway, OAuth, zero trust. ↩︎
- Roadmap.sh API Security Best Practices – Checklist for auth, input, JWT, OAuth. ↩︎